Deep Packet Inspection and Polymorphism
Packet Inspection
Depth of Packet Inspection
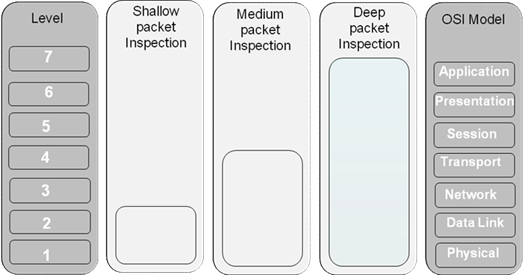
Deep Packet Inspection(DPI)
- Most network flows are not correctly classified using port-based classification(traditional packet inspection)
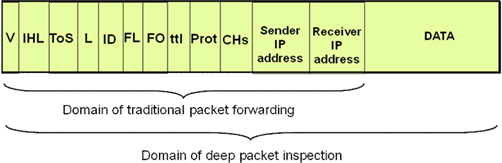
- Deep packet inspection: check the payload of the packets, and handle the packets based on specific patterns present in the payload
- Applications
- Network Security
- Malicious URLs/websites
- Malicious payload
- Inside data loss prevention(DLP)
- Signature detection
- Bandwidth Management
- User Profiling/Ad Injection
- Billing and Metering of Traffic
- Information Regulations and Filtering
- Copyright Enforcement
- Government Surveillance and censorship
- Challenges
- Performance bottlenecks at OS and hardware levels
- Hard to scale with high speed links
- Massive and variable feature signatures
- Encrypted traffic
- Polymorphism of payloads
- Privacy and legal concerns
Evade Deep Packet Inspection
- Traffic Obfuscation
- Encryption and Tunneling
- Polymorphism
- Interleaving meaningful instructions with DO-NOTHING instructions
- Using different instructions to achieve the same result
- Shuffling the register set used in each version of the polymorphic decryptor
- Decrypting and reencrypting parts of the polymorphic decryptor as it is being executed
- Using several layers of decryptors
References

